I looked at it when it started to rise last summer, but back then it was not very adwanced and looked to had stolen most of the code from other EK's.
But several have mentioned lately that it had started to use stegonografy and also weaponized with new exploits.
@Kafeine - CVE-2016-7200 & CVE-2016-7201 (Edge) and Exploit Kits
@TrendLabs - Updated Sundown Exploit Kit Uses Steganography
So lets see under the hood of Sundown EK anno 2017
I just reached out to malware-traffic-analysis for a recent pcap.For reference I have added the output from wireahark showing what was requested from the client. So it will be easier to see what actions have been taken by the EK code. More details over at malware-traffic-analysis.
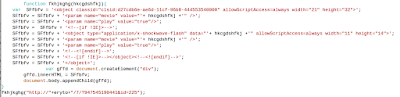
Landing - As always some obfuscation trickery
The landing seem still to spray out what ever its got and hope that something will stick to the client.
3 Flash files are set for download and a mysterious image.
Landing - Flash 1
Code for loading the flash file. At the bottom we also see the url for the payload. We can confirm that this flash was successfully run as we also see from wireshark that the payload url was requested from the client.
Landing - Flash 2
Landing - Flash 3
Even more flash. Looks like some shellcode is provided at the bottom too... which it probably is and the payload url added. If we unescape the hexstring:
Pobably cve-2015-7645
Landing - png stegonografy
To what we really have been waiting for. Stegonography in real life. Awesome. Finally we can use the skills we have been training in all those CTFs?
Nice white little image there
OK, so the image is loaded
And things are done with the image
We better use some vodoo on this image file then and see whats hidden inside.
png file decoded
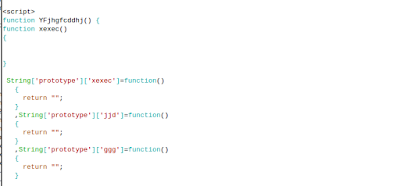
What else. Moar JavaScript of course.
The same shellcode pops up again.
This looks like old IE exploit code from sundown. Maybe the new exploits where not added when this pcap was taken?
Pobably cve-2015-2419
Payload - encrypted and in clear
Strangely sundown EK provides payload both in encrypted form and in clear.
As seen payload in clear.
And payload RC4 encrypted.
After RC4 decryption.
Epilogue
Encryption of payloads have started. Maybe sundown will discontinue the clear text download of payloads in the future.
Using Stego is at least a cool feature.
Sundown still seem to be gready and just throws all exploits it got at you, hopes that something will be successful and downloads payloads in various formats after that.
As @Kafeine reported new exploit added recently. Maybe there will be a fight between Sundown and Rig for the EK throne in the weeks and months to come?
Todo: look more into the flash files for details. Out of luck finding the newly announced exploits so I guess I need another go soon.
No Python coding needed for this task(RC4 decryption only, but that code was on disk already) so we have to fill the void with som diffrent Python: Monty Python. Nice to blog so I could look through some old stuff again. What better than the TrojanRabbit? Enjoy!
Happy Sundown EK hunting
@malforsec